Security
How we ensure your charger is completely secure
Three facets of EV charger security
In order to keep our EV charges secure, our software security engineers focus on three crucial tiers of security: The connection from the charger to the charge point operator, the WLAN access point and web interface access control, and direct memory access.
Connection from the charger to the charge point operator (CPO)
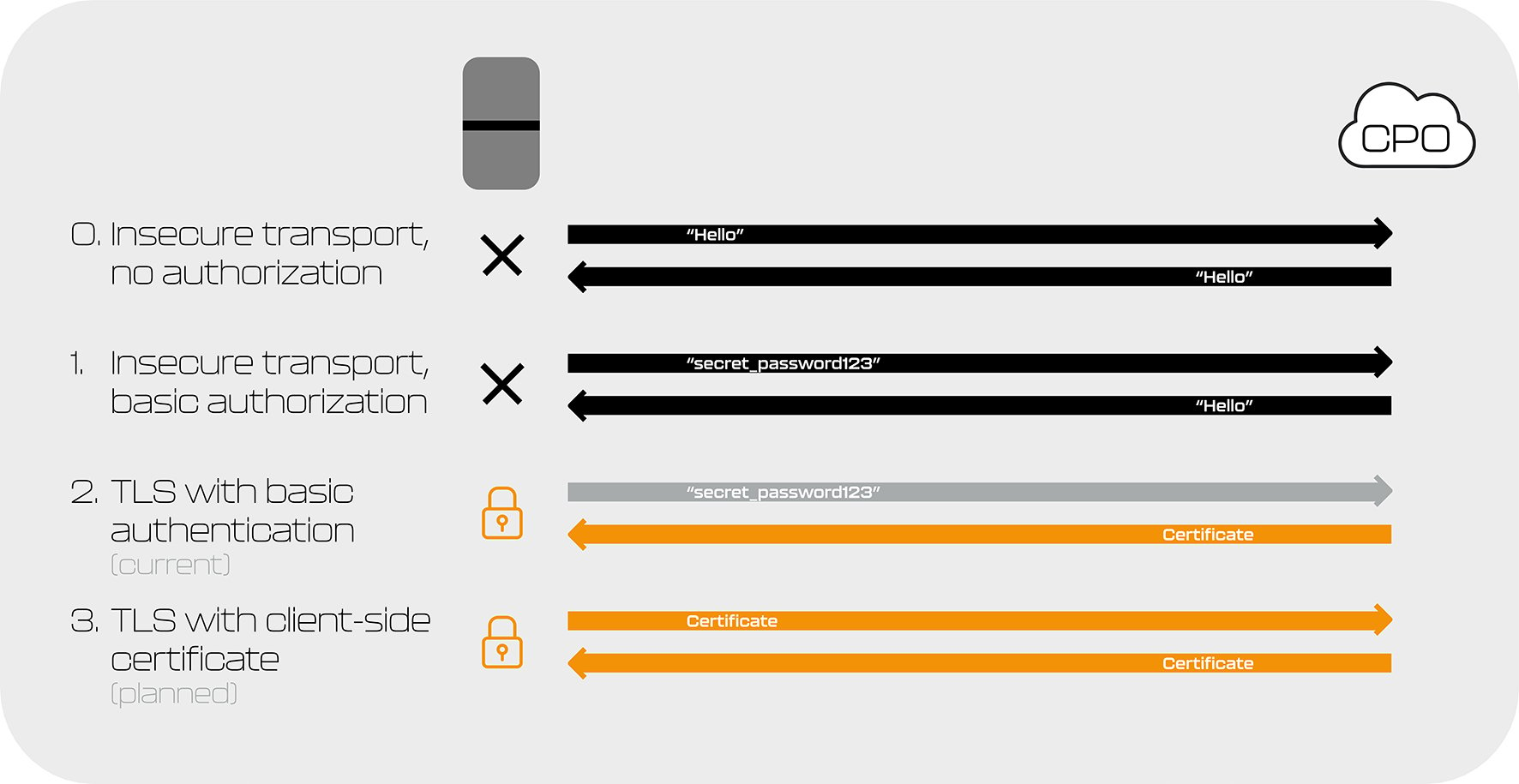
Peblar EV chargers connect to CPOs over an encrypted connection through a digital certificate and password. While other options are available and enable easier connection between chargers and CPOs (for example, just with password access), we use a more secure method to keep our chargers and users safe.
Future updates
We are also planning to implement a future update to our connection that allows connection over an encrypted connection through a digital certificate going both ways, otherwise known as mutual digital certificates.
WLAN access point & web interface access control (via AP or ethernet)
Each charger has unique passwords and all charges exit the factory with robust, randomly generated passwords for:
Web interface login password
Web interface PUK code
Access point network password
OCPP authorisation password
Passwords are stored using a product secret value within a secure subsystem of the internal manufacturing framework.
Direct memory access (physical or remote)
Our EV Chargers are built to only trust the software they come with. There is no way of installing external firmware onto a charger, and to keep the charger extra secure, test software also can’t be installed.
Once the charger goes through end-of-line programming for a customer, it cannot be changed to another firmware. Each charger is locked to the intended customer and there are no ‘back-doors’ into the charger’s software and no other software can be installed on the charger.
Peblar EV chargers are built to be low maintenance for customers, while remaining secure.
Future-proofing society
At Peblar, we heavily rely on hardware, featuring a secure boot that ensures enhanced security.
We use trusted platform modules to store certificates and cryptographic keys, supporting new algorithms and future-oriented security measures, keeping our software security highly future-proof.
Curious to know more about EV charger security? Dive into our blog right here where Sten, our software security engineer, offers detailed insights.
Software and Security Update Policy
To ensure the continued performance, reliability, and security of your Peblar charger, we are committed to providing regular software and security updates, as technically feasible.
These updates are designed to improve the charger’s functionality, optimize performance, and address any security vulnerabilities that may arise.
Software updates
We will provide software updates for a minimum of three (3) years from the date of manufacture. These updates may include:
- Functional improvements: updates to optimize the performance and efficiency of your charger.
- Additional features: introduction of new features to improve the user experience and the charger’s capabilities.
- Bug fixes: corrections to any issues identified that do not pose a security risk but may affect the charger’s normal use. These fixes ensure that the charger continues to operate reliably and effectively.
Security updates
We will provide security updates for a period of five (5) years from the date of manufacture. These updates are specifically designed to address and mitigate critical security vulnerabilities through software patches or other mitigation measures necessary to ensure your charger remains safe and secure against potential cybersecurity risks.
To keep your charger secure, always install the latest software version. Keeping your charger up to date ensures that all features and security measures are fully operational.
