Hacking an EV charger - what could possibly go wrong?

At first glance, hacking a charger doesn’t seem like a lucrative activity. It’s just a charger; what could possibly go wrong? “A lot,” says Sten Verbois, Software Security Engineer at Peblar and responsible for the security of all white label and Peblar chargers.
“People with bad intentions can hack the grid via chargers and solar panels and cause serious damage to companies and entire countries.” This statement is backed up by a large number of recent news articles, including the one in Wired, which stated that “EV charger hacking poses a ‘catastrophic’ risk.” In the article, the author describes a wide range of possible hacking scenarios, from showing political messages on the display and stealing credit card information to causing a nationwide blackout.
“Still, hackable IoT infrastructure seems to be the norm,” Sten says. "Securing EV chargers appears to be more of an exception than a rule." He does understand why this is. “Many businesses and CPOs think charger security is a nuisance,” he says. “Security has the reputation of being high maintenance and slowing down innovation. When people aren’t aware of the perils, as is the case with EV chargers, they tend to risk it.”
And that’s a problem?
Sten: “That’s a problem.”

Not all is lost
There’s good news, too. “The industry is working hard,” Sten says. “And there’s the EU Radio Equipment Directive on cybersecurity, data protection and privacy, which will be mandatory from 2025. Also, there’s the Cyber Resilience Act, for which a proposal has been submitted in 2022.” With increasing awareness and legislation in the making, EV charging security is moving in the right direction. Sten: "However, this doesn't imply that businesses and CPOs will soon be burdened with numerous measures that could impede their operations. At Peblar, for instance, we’ve invested a lot of effort into fortifying our chargers in a way that’s highly manageable.”
The three facets of EV charger security
With his team, Sten fortified their defence across three facets:
- Connection from the charger to the Charge Point Operator
- WLAN access point and web interface access control
- Direct memory access, physically or remote
Below, Sten talks us through the options and explains the choices he and his team made to optimally secure all Peblar chargers.
1. Connection from the charger to the charge point operator
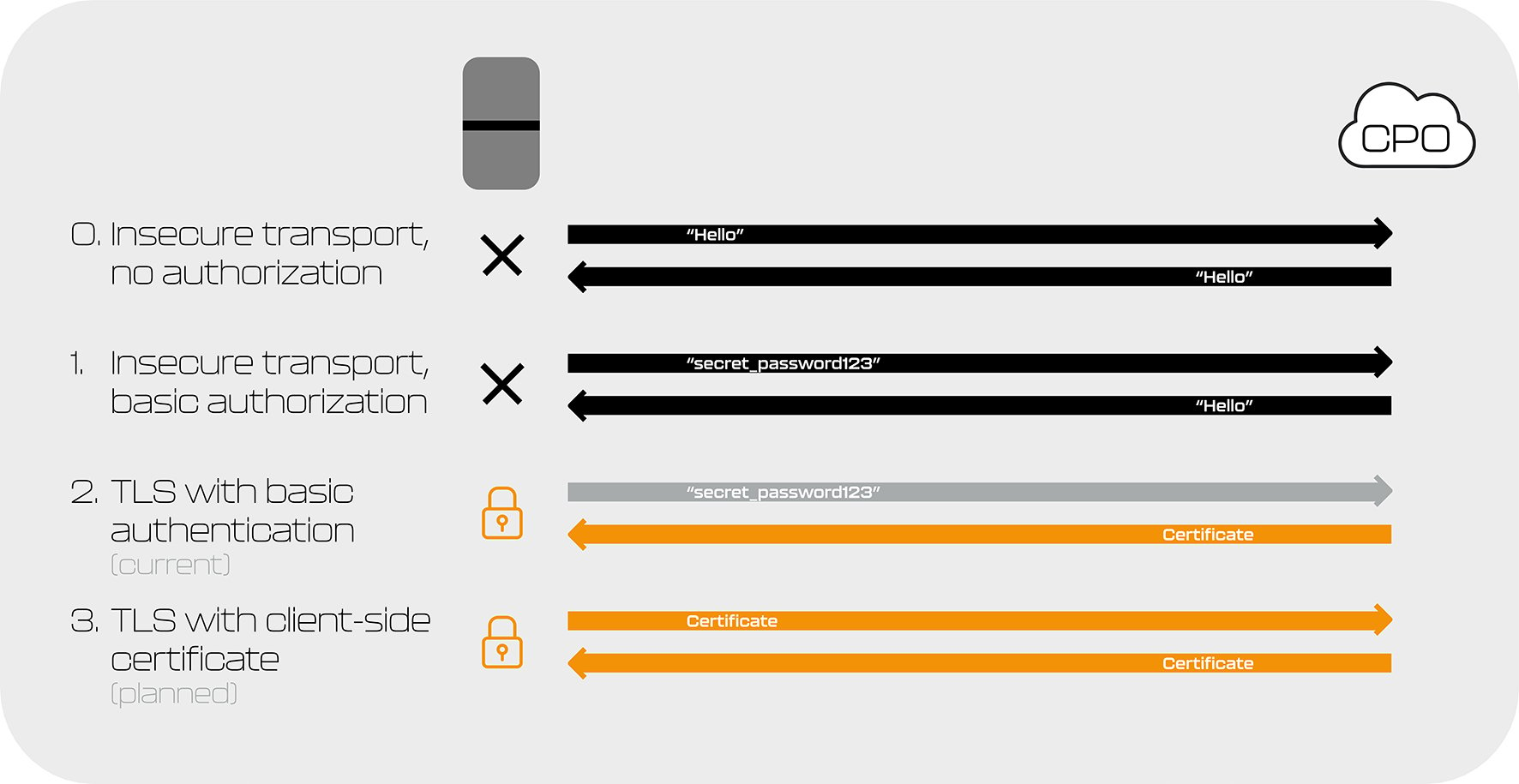
There are four ways in which you can connect a charger to a CPO. These are:
- Profile Zero - Over an insecure connection, without any authorization
- Profile One - Over an insecure connection, with a basic password
- Profile Two - Over an encrypted connection using a digital certificate for the server and password for the client
- Profile Three - Over an encrypted connection using a digital certificate for both parties
Sten: “We don’t work with profiles Zero and One at all. We only support Profile Two, and we’re ready for Profile Three, which will be available in the near future. We don’t even use profiles Zero or One for testing to avoid accidentally enabling an insecure connection in the field. It’s very easy to misconfigure this, so we’re rather safe than sorry.”
2. WLAN access point & web interface access control
Sten emphasises, "We generate unique passwords per charger and avoid default passwords." Chargers exit the factory with robust, randomly generated passwords for:- Web interface login password
- Web interface PUK code
- Access point network password
- OCPP authorisation password
"We store these passwords in a secure subsystem of our internal manufacturing framework." Sten elaborates. “We do everything we can to reduce the time that passwords are exposed. They are accessible exclusively in the production steps where they are required.”

3. Direct memory access, physically or remote
Either when you plug something in on the charger or if you remotely access it, you gain access to the charger memory. The easiest way for hackers to hack a charger is, therefore, to upload their own malicious software. Sten: “We make sure the charger only trusts the software that we provided.” He and his team enable ‘Secure Boot’ on the product by making use of a region of one-time-programmable memory to store trusted information.
Sten: “This process is irreversible, so no non-trusted software will ever be installed. He often gets the question of whether it’s possible to put test firmware or a customer’s firmware on a charger that was initially produced for another customer. Sten: “The answer is a clear no. Once a box goes through end-of-line programming for a customer, it cannot be changed to another firmware. Allowing such modifications after production would mean they’re also possible in the field by malicious actors.”
All service back-doors will be discovered eventually, and used and abused in the field”

What are the implications of strict security rules?
Going back to the initial question of this article: how much effort is required from customers, given the many strict rules that were implemented by Sten and his team? Sten: “Sometimes, our security policy makes things more difficult during development. For example, passwords are stored in a secure subsystem, so we cannot retrieve the access point login for any box in the field. Also, thanks to Secure Boot, switching to test, service, or different customer firmware is not possible after finalising production. We make sure we prevent placing ‘service back-doors’ in the charger. After all, these back-doors will be discovered eventually and used and abused in the field.”
Ideally, our customers don’t notice our security solutions at all; they simply receive a secure product”
Apart from these implications, the solutions Sten implemented are actually very low maintenance. “Ideally, our customers don’t notice them at all,” he says. “They simply receive a secure product. They’ll notice there are several different passwords, which takes a little more effort at the start. But we aim to limit this number to a minimum and have the product just work securely.”
He adds: “Sure, not doing any security is easier. But working with digital certificates is such common practice. Just think about website URLs: you almost never see an insecure website URL anymore. The additional effort for the CPO is quite limited.”

Future-proofing security
Apart from his role in the software team, Sten also bears the main responsibility for Prodrive Technologies product cyber security in general, including system design. Sten: “I like to stay updated on technical cyber security matters and depend on sales engineers to understand what customers want and system architects to identify their system requirements.”
He continues: "Security is a fusion of hardware and software. At Peblar, we heavily rely on hardware, featuring a secure boot that ensures enhanced security. Additionally, we use trusted platform modules to store certificates and cryptographic keys, supporting new algorithms and future-oriented security measures. Thus, Peblar's hardware security is highly future-proof. As for the remaining aspects, they’re addressed through software."
“At Prodrive Technologies, the foundation always revolves around creating excellent hardware. With our extensive experience in building high-quality hardware, we’re well-versed in adhering to strict automotive standards. This valuable experience and expertise can be applied to Peblar, giving us a significant advantage.”
